SCC
Brasil
os cloud gurus
Software Cloud Consulting
Your software development, cloud, consulting & shoring company
VPC IPv6 - Running EC2 Instances

By Wolfgang Unger
Introduction
Are you getting started with IPv6? How to run EC2 instances in a IPv6 VPC?
Lets answer these questions in here.
In the last blog we created a IPv6 VPC.
You should have a VPC as precondition for this tutorial and it should have subnets with IPv6 CIDR range.
If not, take a look into this blog for a introduction and how to setup a IPv6 VPC.
VPC IPv6 Introduction
Our VPC:
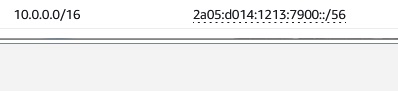
Subnets:
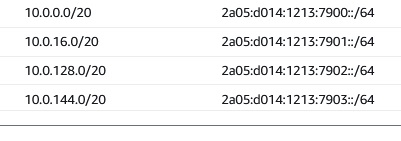
Now its time to test, its working.
Let's start with the EC2 and see if we get everything working.
Reminds me of 10 years ago, when I started to work with AWS.
Of course, the first thing I tried out, was to launch a EC2 instance.
Running EC2 Instances
We will use the Web Console for our first tests.
IaC will follow.
So switch to EC2 and press 'Launch Instance'
We have to configure a little for our IPv6 Network.
First, you must select a t3 instance or other new instance type, a t2 will not work.
I will select t3.small
Choose an existing keypair ( or create one)
Edit the network settings, select your IPv6 VPC and for now lets place the instance in the public subnet.
For connectivity tests let's both enable Auto-assign public IP and Auto-assign IPv6-IP
Select an existing security group or create one.
Depending on the tests, you must define the inbound rules, I will for now open SSH, HTTP, HTTPS and ICMP - IPv6 (for Ping)
To keep it simple for our fist test ( this is not a secure production setting) let's open for
these protocols the communication to the internet by adding this IPv6 CIDR Range:
::/0
Settings:
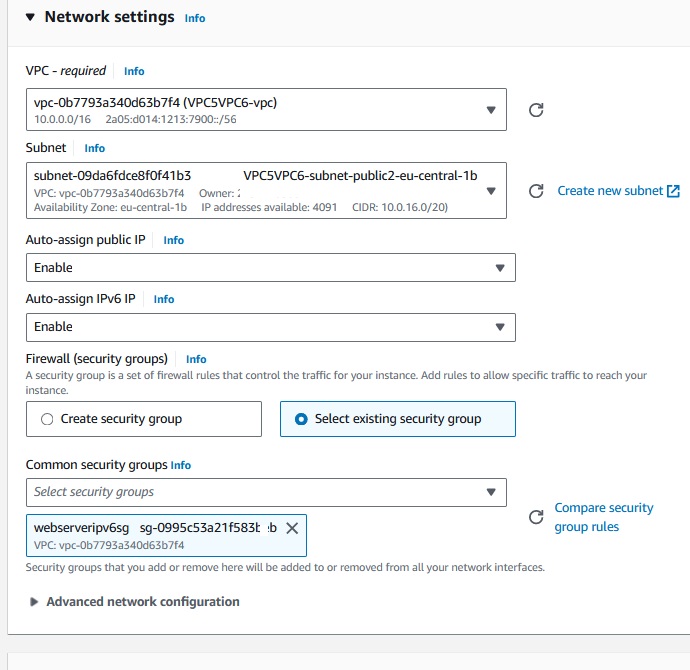
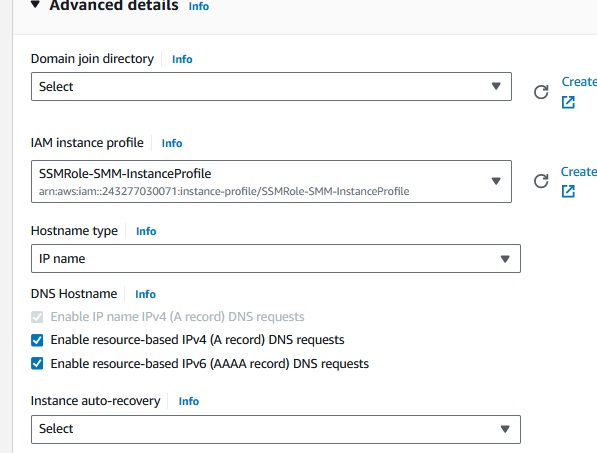
You should also add an instance Role to allow SessionsManager to connect to the instance (AmazonSSMManagedInstanceCore)
Enable also resource-based IPv6 (AAAA record) DNS requests ( and optional ) resource-based IPv4 (A record) DNS requests
Once the instance is launched, lets take a look in the instance details
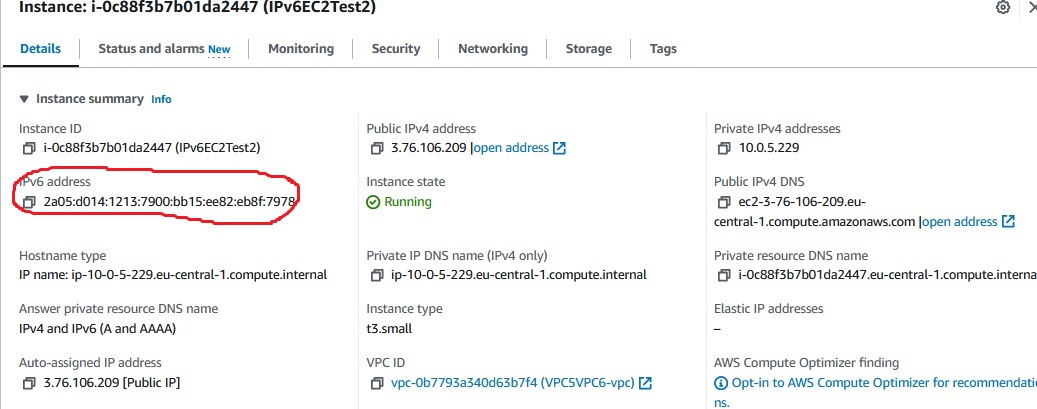
Important for us right now the IPv6 address:
2a05:d014:1213:7900:bb15:ee82:eb8f:7978
Connect to EC2 Instances
Lets see, if we can connect to our instance now.
We will connect with the IP address for now.
For DNS keep in mind:
When you launch a EC2 in a IPv4 VPC with IP address-based naming it will recieve a name like ip-10-20-14-8.ec2.internal
For IPv6 Subnets we need Resource-based naming (RBN).
The format for an instance in any AWS Region is: ec2-instance-id.region.compute.internal
For example: i-0123456789abcdef.us-west-2.compute.internal
First I will try the AWS Cloud Shell and a ping on the IPv6 address
I am getting this error : Network is unreachable
SSH also does not work with IPv6 address.
So it looks like, we cannot connect with AWS Cloud Shell .
Lets try Sessions Manager.
Keep in mind for Sessions Manager this statement from the AWS Documentation
IPv6 security and monitoring considerations
"Resources managed by AWS Systems Manager must have IPv4 connectivity to Systems Manager’s endpoints.
For example, to connect to an EC2 instance using Systems Manager Session Manager, the instance must be running dual-stack and
must have an IPv4 connectivity to the internet or AWS PrivateLink VPC endpoint. Similarly, on-premises resources must also be in dual-stack network mode."
So we will actually connect still with IPv4 to our instances, since we will have a dual stack VPC it should work.
If you setup IPv6 only subnets, follow this instructions
SSM public endpoints
You will have to enable DNS64 (returns AAAA records with these synthetic IPv6 addresses for IPv4-only destinations)
and also for your private Subnets add a Engress Only IGW or NAT ( here we go again).
By the way, you can also setup a VPC endpoint to connect to your EC2 instances with Sessions Manager and not use the public endpoint.
See this documentation:
Create VPC endpoints
Therefor you open the VPC Console, then endpoints and press 'Create endpoint' and
create Endpoints for these services:
ssm.region.amazonaws.com, ssmmessages.region.amazonaws.com, ec2messages.region.amazonaws.com.
I will try this for my IPv6 VPC but as you can see, IP address type IPv6 and Dual Stack is not available (maybe not yet):
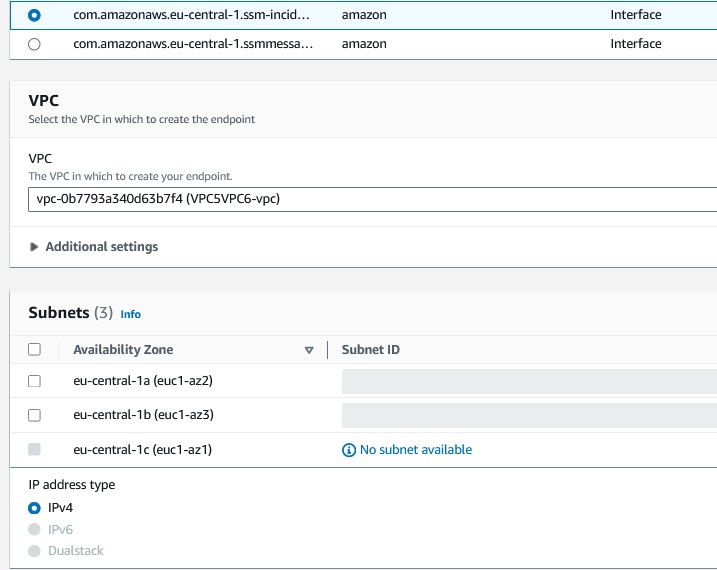
Lets skip this part for now and try to connect with IPv4 functionality.
I had issues to connect with the instance when selecting the instance and press Connect, then switch to the Sessions Manager TAB.
I recieved an error the role is not sufficient ( even so was attached correctly).
But looking in the Sessions Manager, the instance would appear in the possible targets, when you press 'Start a session'
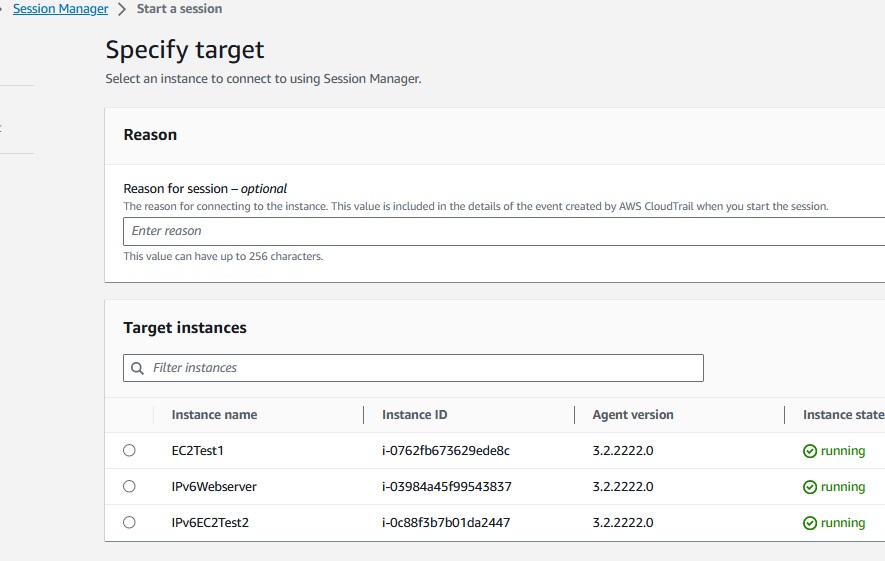
After connect to the instance in Sessions Manager,
the option to connect via the intance and 'connect' was also healthy.
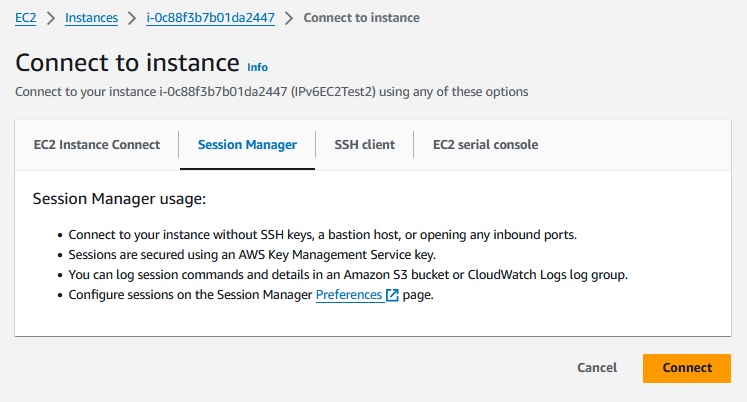
So we can connect with sessions manager, that's perfect.
If the connect option doesn't work the first time, use the SessionsManager. Looks to be a workaround for now.
let's also try SSH into the machine, we can use this command:
ssh -i "wolfgang.pem" ec2-user@2a05:d014:1213:7900:476d:4f16:ffe0:ee16
So, besides the IPv6 address no change.
Now lets try to start a second instance and ping the instances.
Copy the IPv6 from the second instance and connect with sessions manager to the first instance
and you can ping the second instance by
ping6 2a05:d014:9be:9396:f365:96f6:8c78:c1ba
(ICMP - IPv6 must be open on the Security Group)
The ping will also work, if you setup all correctly.
You can also ssh into the other instance if you upload the pem file on the machine for this test.
We can also test if our VPC is working by EC2 instances.
Connect to a instance in the public Subnet and try a wget or curl command to an internet address.
It will work.
For the same test on a instance in the private subnet we need to jump over the instance
in the public subnet (which we can access by SessionsManager and IPv4) and then SSH into the
instance in the private Subnet. Both most have the same Keypair and you must upload the Keypair to the public instance.
Once you are on the private instance, you will see, that curl and wget also works, thus our Route Table and EngressOnly IGW was setup correctly.
Setup HTTP/HTTPS
Now lets connect to one of our instances and install apache. These lines will do :
#!/bin/bash
sudo yum install -y httpd
sudo chkconfig httpd on
sudo service httpd start
No we connect again to the 2nd instance ( via sessions manager or ssh ) and try to curl the webserver
curl -g -6 'http://[2a05:d014:9be:9396:f365:96f6:8c78:c1ba]:80/'
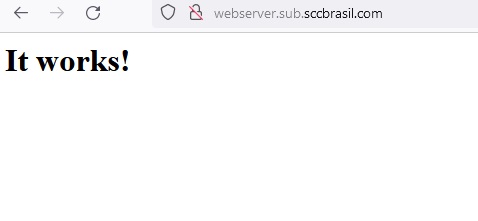
And we will get a :
"It works!" in HTML
We can also call the Webserver from our Browser by typing:
http://[ipv6-address]/
for example:
http://[2a05:d018:16e5:e200:8910:89f0:9df3:6b98]/
Perfect, lets see if we can also route from Route53 to our instance.
If you have a domain and HostedZone you can test this.
In you HostedZone create a new RecordSet of Type AAAA, non Alias and enter the IPv6 address as value.
In my case this is webserver.sub.sccbrasil.com and by now I can also call my webserver from my Browser:
EC2 in private Subnet
Time to test, everything works as expected also with an instance in a private Subnet.
We launch an instance the same way, but this time we select one of our 2 private Subnets of our IPv6 VPC.
I can ping the private instance from my instance in the public subnet, this works fine.
I can also SSH into the private instance.
So communication between the instances works like a charme.
I will try to connect with Sessions Manager.
The button to connect is not enabled and also the workaround directly in Sessions Manager doesn' help.
The instance does not appear in the targets.
But we know already the reason.
The Sessions Manager connects with IPv4 over a public enpoint ( or a VPC endpoint which we could not create for IPv6)
and our private Subnet got no Engress Only IGW or NAT.
So I change my Subnets following the documentation for these values:

and add a Engress Only IGW and add the routes for it.
But still I cannot connect to my instance.
The SSM Agent requires IPv4 access to Systems Manager endpoints in order to function, it is not yet ready for IPv6.
So Sessions Manager is still an issue with IPv6.
Hopefully the SSM Agents gets an update soon.
Finally I will try if I can route from R53 also to my private instance with an AAAA record to its IPv6 address.
I install a webserver on the instance an create a new route http://webserverprivate.sub.sccbrasil.com/
and open the Security Group for port 80.
This works also, we can route from Route53 to our instance in a private Subnet over the IPv6 address.
IaC
First examples for CloudFormation are already available, but the repo is in work, keep that in mind.
Stay tuned !
The repo (under construction) is :
Github Wolfgang Unger - AWS IPv6
Conclusion
Besides the Connect issue there were no relevant problems.
Sessions Manager is not IPv6 ready.
Connection works fine, you can communicate between instances, SSH into machines or use Sessions Manager and setup a Webserver for example.
For the next blog, I'm going to have a look on other AWS services, like Elastic Beanstalk, Fargate and others
how these work together with IPv6 .
Stay tuned !
The blog for introduction and how to setup a IPv6 VPC.
VPC IPv6 Introduction
Autor

Wolfgang Unger
AWS Architect & Developer
6 x AWS Certified
1 x Azure Certified
A Cloud Guru Instructor
Certified Oracle JEE Architect
Certified Scrum Master
Certified Java Programmer
Passionate surfer & guitar player