SCC
Brasil
os cloud gurus
Software Cloud Consulting
Your software development, cloud, consulting & shoring company
S3 Block public access VS Terraform/Cloudformation
By Daniel Nascimento
Since April 2023, AWS has change the default configuration of new buckets to "Block public
access",
not only to buckets created using the aws console UI, but also for buckets created using AWS
CLI, SDK and
Cloudformation too.
This change means that if you have a terraform project or a cloudformation template that creates
new buckets in your aws accounts,
you probably have to change your code to deal with this new behavior.
If you simply apply your previous terraform code or cloudformation template, your bucket
policies probably are not gonna be effective,
if you have some kind of public principal (federated users for example) or use a "*" without a
condition that filter these principals,
or use ACL's.
AWS Documentation : What AWS consider "Public"
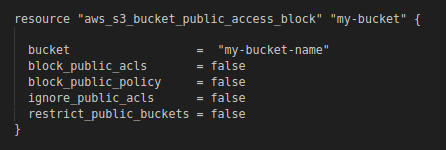
To return to the previous behavior (without the block public access), you have to do some
changes to your code, if you want to have the "Block public access" disable in Terraform just
use the "aws_s3_bucket_public_access_block" resource, example :
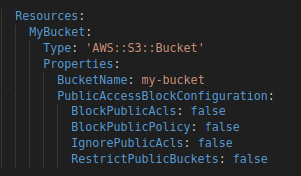
In Cloudformation the same can be accomplished using the PublicAccessBlockConfiguration property
in the AWS::S3::Bucket resource. example:
This change also can be a opportunity to review the permissions in your buckets and maybe enable
some of the block access options, and ensure a secure storage to your data.
Autor

Daniel do Nascimento
Cloud Developer
3 x AWS Certified